Saturday, October 25, 2008
Pass4Sure 640-802 v3.22
Exam Name: Cisco Certified Network Associate
"Cisco Certified Network Associate", also known as 640-802 exam, is a Cisco certification.
Preparing for the 640-802 exam? Searching 640-802 Test Questions, 640-802 Practice Exam, 640-802 Dumps?
With the complete collection of questions and answers, Pass4sure has assembled to take you through 254 Q&As to your 640-802 Exam preparation. In the 640-802 exam resources, you will cover every field and category in CCNA helping to ready you for your successful Cisco Certification
Link Download
Pass: http://networkstepbystep.blogspot.com/
Friday, October 24, 2008
CCNA 4.0 final Question and Answer
1. CCNA4 Module 1
2. CCNA4 Module 2
3. CCNA4 Module 3
4. CCNA4 Module 4
5. CCNA4 Module 5-1
6. CCNA4 Module 5-2
7. CCNA4 Module 5-3
8. CCNA4 Module 6
9. CCNA4 Module 7
9. CCNA4 Module 8
Updated 19/7/2008
CCNA4 Final 100% (update 21/7/2008)
Monday, October 20, 2008
PIX Lab: Tutorial in PIX
- Basci PIX Configuration
- Installing WebSENSE
- Config NAT Stats and Conduits
- Config Multiple Interfaces
- Config Authentication
- Config the Primary PIX Firewall
- Verify IPSec Configuration
- Passwrod Recovery & Image Update
- Configuring the CSIS Feature Set
- Configure Cisco Secure ACS NT
- Configure AAA and Authentication Proxy
- Verify Authentication Proxy Configuration
- Configure the PIX as a DHCP Server Configuring PIX as a DHCP Client
- Configuring Logging
- Configuring Logging -Verification
- Denying Outbound Traffic
- Allowing Outbound Traffic
- Configure PIX to work with Websense
- Configure WebSense to Block by URL
- WebSense to Block by Workstation
- Configure the Fixup Protocol on PIX
- Configuring PIX for IDS Signatures
- CSACS Install and Add User
- Configure IKE and IPsec on the PIX
Let visit this thread in forum to download
Thursday, October 16, 2008
How to build a secure Enterprise Firewall?
What is the most important aspect?
There has been some fierce debate in design philosophy on whether it is best to have one brand of firewall or more. I personally subscribe to the idea that two are usually not better than one because firewall vulnerabilities are rarely the problem in vast majority of break-ins. Hackers typically don’t need to hack the firewall because they come in through the ports that are already open and exploit the weaknesses on the servers behind the firewall. Additionally, there usually is nothing there for the hacker to hack on the firewall, because any smart administrator will lock that firewall down to drop all connections to the firewall it self except for the designated firewall management stations. Even if for example there is a known vulnerability in Apache or SSH on your firewall, the threat can only come from the designated management stations which are well protected or even turned off
1. Human factors comprises 99% of all firewall compromises
2. The cost of running multiple vendor firewalls may even force you to give up on the very things you need to be most concerned about.
3. Finite resources are usually much better spent hardening a single platform.
4. The biggest problem in firewall security is poor maintenance, bad policy and bad network design
Firewall design goals:
A good firewall policy and network design can mitigate (but not eliminate) the following security risks:
- The Internet attacking your DMZ servers
- Any part of your network attacking the Internet
- Your users or servers attacking your DMZ servers
- Your DMZ servers attacking your users, servers or even further harming them selves
- Threats from business partners and extranets
- Threats from remote offices via WAN connections
The first point is rather obvious; simply by limiting the service port access from the Internet to your DMZ servers, you can greatly reduce the chances that they will be hacked. On an SMTP mail server for example, only TCP port 25 is permitted from the Internet. Therefore, if that SMTP server happened to have a vulnerability in it’s web server service or daemon, it would not be exposed to the Internet where worms and hackers are always on the prowl for port 80 vulnerabilities.
The next point may seem a bit odd, why would one be concerned about protecting the public Internet with one’s own network? While this may seem to be just a good exercise in Netizenship (Internet citizenship), it is also for the selfish purpose of protecting one’s own Internet connection. Take the recent SQL slammer worm for instance; it managed to decimate large segments of the Internet for an entire day. Had there been better firewall policies in place, you could have prevented the DoS (Denial of Service) effect on your Internet connection and also saved the Internet.
One of the least recognized dangers in security is the internal threat. The most expensive firewall on the planet cannot protect your network from “Sneaker net” with conventional designs, a phenomenon where your user walks in to your network with a laptop or disk infected with a virus or worm from home or some other source. A good network design and firewall policy would protect your DMZ servers from your servers and users the same way it protects them from the Internet.
The reverse situation of the above is also a potential threat. Since DMZ servers are exposed to the public Internet, there is a chance that they can be compromised by a hacker or worm. It is essential that you limit the damage that your DMZ servers can do to your internal servers or user stations. Additionally, a tight firewall policy can also prevent DMZ servers from further damaging them selves. If a server is compromised by a hacker through some known or unknown vulnerability, the first thing they will try to do is down load a “root kit”. The firewall policy should prevent the downloading of this deadly payload and make life harder on the attacker.
Additional threats from Extranet partners and Remote office WANs can also be mitigated. Routers that connect these networks using WAN technologies such as frame relay, ISDN, private lease line, or VPN tunnels can be secured by the firewall. Trying to implement security with firewall enabled routers on each and every one of those routers is expensive not only in terms of hardware/software costs, but setup and administration as well. An enterprise firewall can provide simple and centralized management of WAN and Extranet security with additional zones beyond the conventional triple homed design.
The bottom line is that firewalls can limit the flow of traffic between network zones which are broken down by logical organization and functional purposes. A firewall cannot however limit and protect hosts from other hosts within the same subnet because data never passes the firewall for inspection. This is why the more zones a firewall supports, the more useful it is in a well designed enterprise network. This is now easier than ever to accomplish since all of the major players like Cisco and Nokia support trunking of interfaces. A single gigabit port can easily support as many zones as you like and still perform much better than several fast Ethernet ports.
Implementing a good firewall policy:1. The first critical component of secure firewall architecture is policy design.
In firewall policies, this simply means that unless there is a specific reason that a service needs to be used, that service should be blocked by default.
To implement this default service blocking policy, only one simple firewall rule needs to be implemented globally at the end of all policy sets, the any-any-any-drop rule. This simply means that the default behavior of the firewall will drop all packets from any source to any destination on any service. It is important that this rule is the last rule in any policy set because firewalls act from top to bottom.
==> The narrower these rules are made, the more secure the network is.
For example, users should be permitted outbound ports for common services like HTTP, FTP, media services, but nothing else should be permitted unless there is a special case to allow such traffic. When there is a special case based on a business need, tightly targeted rules should be added when approved. A very common error that administrators make is that they extend user rights to server and DMZ networks. Outbound rules that are appropriate for users are generally not appropriate for servers. When you really think about it, there is no reason that your Web server needs to surf the Web. Servers should serve and are rarely a client. The bottom line is, the DMZ or Server farm should almost always never be permitted to initiate traffic. Servers typically take in requests, but almost never request services from the public Internet except for XML and EDI applications with business partners. Other exceptions can be things like legitimate vendor sites that provide drivers and software updates, but all exceptions should be narrowly defined. Following these strict guidelines can vastly reduce server compromises, to the point that even the intra-subnet spread of worms like Code Red and NIMDA could have been prevented had such policies been in place even if the servers were not patched.
Implementing a good firewall network design:


Figure 1 illustrates a Pix 525 with 2 Gigabit Ethernet ports and 6 100-Mbit Fast Ethernet ports. This is a great way to achieve physical separation of the different subnets needed for an Enterprise network, provided that each port is plugged in to a physically different Ethernet switch. How ever, I can tell you that this is rarely done and is often impractical to deploy more than half a dozen physical switches in the data center for each subnet. More often than not, enterprises employ virtual LANs by segmenting a single physical switch in to multiple bridge groups, which is extremely easy to provision addition ports for any existing subnet or future ones. Because of this and the fact that all the enterprise firewall vendors have added 802.1q trunking support (Cisco came late in February 2003), one can easily use a single Gigabit port to connect the Layer 3 core switch, DMZ, extranet, guest subnet, and any other VLAN subnets that an enterprise needs. Therefore, one can do with out the second Gigabit Ethernet card and 4 port Fast Ethernet card in the PIX 525 shown in figure 1. This has how ever raised need for Layer 2 switch security against things like “VLAN hopping” which is rarely discussed even among experts, but we shall leave that for another piece. But even with the trunked Gigabit port, you should continue using the two built in Fast Ethernet ports for public Internet and stateful failover synchronization. Bottom line, two firewalls in the same class as a PIX 525 can provide enough flexibility and throughput for most enterprise networks.
Figure 2 illustrates the use of the two firewalls in a stateful failover configuration. Network connections were only drawn to the logical firewall to avoid messy connectors in the drawing, but in reality there would be a physical connection to each firewall for each subnet. Those connections could be physically separate cables or a single trunked cable over a single Gigabit connection in to your 802.1q VLAN capable switch. The two built in fast Ethernet ports in a PIX 525 are used for the public Internet connection and the stateful failover synchronizing, and the remaining internal subnets can share the Gigabit port. This configuration is much faster than a configuration with separate fast Ethernet ports that often get congested when trying to do network intensive tasks like tape backup between zones.
The internal side of the firewall can connect the following subnets:
- Core layer 3 switch
- DMZ
- Extranet and WAN
- Guest zone
- Others
The core layer 3 connection typically goes to your core switch with routing capability between VLANs. Those VLANs from that core switch may contain hundreds of user VLANs with tens of thousands of users, and server farm VLANs with hundreds of servers that do not get direct Internet exposure. You must understand how ever that there is no firewall between the server farm VLANs and the user VLANs in this example, because user to server traffic is routed by the core L3 switch and never passes through the firewall. There are companies that go to the extreme of putting all of their servers directly behind the firewall and separated from the users, but the management of that many internal servers behind a firewall with a lot of port requirements can be very difficult, so this is not often done.
DMZ is used for servers that need to be accessed from the public Internet. This is directly behind the firewall and is always filtered for traffic.The Extranet and WAN zone is for the internal interfaces of routers that connect the remote WAN sites and partner sites. Using this configuration allows you to secure against WAN and Extranet sites without having to buy or configure firewall feature sets on the routers them selves. One can even go to the extreme of putting the external interfaces of the routers in a non-NAT zone on the firewall, this helps prevent hackers from compromising the router from the outside. This approach allows the high availability enterprise firewall to secure countless routers.
The guest zone is something new, but this is actually a security feature. Instead of guests connecting to your internal LAN when they need access to VPN or the Internet, have them connect to a guest network with access to the Internet but not your internal LAN. This new zone is extremely useful in the wireless environment. With new Wi-Fi infrastructure technology supporting VLANs and 802.1q trunking, a single wireless Wi-Fi infrastructure can support multiple VLANs, one internal VLAN running it’s own SSID and 802.1x/EAP security, and a guest VLAN that runs a simple WEP password for Internet only access.
VLAN SECURITY
VLAN INSECURITY
VLANS WERE CREATED TO ISOLATE LANS, BUT NOT FOR THE PURPOSES OF SECURITY
Virtual LANs (VLANs) make it possible to isolate traffic that shares the same switch, and even groups of switches. The switch designers had something other than security in mind when they added this form of isolation. VLANs make it possible to share a switch among many LANs, by filtering and limiting broadcast traffic. But this form of isolation relies on software and configuration, not the physical isolation that security people like myself really like to see.
In the last couple of years, some firewalls have become VLAN aware, so that policies can be created that rely on the tags that identify a packet as belonging to a particular VLAN. While firewalls that are VLAN aware add a lot of flexibility useful to Web hosting sites, the tags that these firewalls rely on were not designed with security in mind. VLAN tags can be created by devices other than switches, and valid tags that will fool the firewall can easily be added to packets.
Let's take a look at VLANs, including how they work, why this has little to do with security, and failures of VLANs to maintain isolation. And, if you decide to use VLANs as part of your security architecture, what you should do to minimize the weaknesses involved.
PARTITIONS
The term "switch" today denotes a device that switches network traffic between interfaces, named ports. But not too long ago, switches were called bridges. Even today, if you read the IEEE standards used in switches, the term inevitably used is bridge. And if you are familiar with the way bridges work, you might want to skip ahead.
You use bridges to connect segments of the same LAN, that is, a local network that does not require routing. The bridge software learns which port that network devices have been connected to by examining the source MAC (Medium Access Control) addresses in the packets that the bridge passes. At first, the bridge
knows nothing, and must distribute all the packets it receives to every port. But over time, the bridge learns how to send packets out the correct interface by building spanning trees, an algorithm developed for choosing the right interface and avoiding loops. By sending packets out on a single port, the bridge reduces overall network traffic. Think of the bridge in highway terms, something that connects different roads, and only passes necessary traffic between these roads.
Although the use of bridges does reduce overall network traffic, making networks more efficient, bridges still need to send broadcast packets to all ports. Just as in any LAN, broadcasts mean just that, a message broadcast to all systems. ARP (Address Resolution Protocol) packets provide an important example of broadcast messages.
As bridge hardware grew more capable, with increasing number of ports and the addition of management software, a new feature appeared. You could partition a bridge, split a single bridge into multiple, virtual bridges. When split this way, broadcasts, instead of going to all ports, get limited to only those ports associated with the virtual bridge, and its virtual LAN.
Limiting broadcasts to a VLAN does not seem by itself to prevent a system on one VLAN from hopping to another VLAN-- that is, contacting a system on the same bridge, but a different VLAN. But remember that broadcasts get used to acquire the MAC address that is associated with a particular IP address, using ARP, and without the MAC address, one system cannot communicate with another on the same network. Routers, or switches that support layer three, support passing traffic between VLANs.
Over time, people have begun to consider switches as security devices rather than networking devices. Switches do make sniffing traffic destined for other systems more difficult (but not impossible, as exploits exist for doing so). And switches do produce a software-based isolation between VLANs. But that isolation is imperfect at best.
In a document found on the Cisco web site (See Resources), two scenarios are described where packets can hop VLANs, that is, pass between two VLANs on the same switch. In the first example, systems have established TCP/IP communications on the same VLAN, then the switch gets configured so that one system's port now belongs to a different VLAN. Communications continues between the two systems because each has the MAC address of the other in its ARP cache, and the bridge knows which destination MAC address gets directed to which port. In the second example, someone wishing to hop VLANs manually enters a static ARP entry for the desired system. Doing so requires that the person somehow learns the MAC address of the target system, perhaps through physical access to the target system.
Each of these two examples can be blocked by using switch software that removes the information necessary for passing packets between VLANs. In higher end Cisco switches, separate spanning trees, the tables that map MAC addresses to ports, exist for each VLAN. Other switches either have similar features, or can use configuration to filter the bridging information available to members of each VLAN.
Given the relative dearth of information about hopping VLANs within a single switch, this issue does not appear to be a serious problem.
TRUNKING
Multiple switches can share the same VLANs through configuration and tagging of the packets exchanged between switches. You can configure a switch so that a port acts as a trunk, an interface that can carry packets for any VLAN. When packets get sent between switches, each packet gets tagged, based on the IEEE standard for passing VLAN packets between bridges, 802.1Q. The receiving switch removes the tag and forwards the packet to the correct port or VLAN in the case of a broadcast packet.
802.1Q tags get added to Ethernet headers right after the source address and are four bytes long. The first two bytes contain 81 00, the 802.1Q Tag Protocol Type. The last two bytes contain a possible priority, a flag, and 12 bits for the VLAN Identifier (VID). VIDs can range from 0 to 4095, but both zero and 4095 are reserved values. The default value for the VID is one, and thus also the default value for unassigned ports in a switch configured with VLANs.
An administrator may configure a port to act as a trunk, although the default configuration for Cisco switches is that trunking is "desirable", and a port can negotiate trunking if it discovers that another switch is connected to that port. And, unless the administrator changes the configuration, a trunk port belongs to VLAN 1, which is called its native VLAN. Ports used for trunking can be assigned to any VLAN, and it turns out that putting trunk ports into a VLAN of their own is a good idea.
In 1999, David Taylor posted information to Bugtraq about tests he had run using Cisco switches, in attempts to force packets to hop VLANs. Taylor first attempted to use VLAN tagging to hop VLANs within a single switch, without success. The VLAN tags really have no purpose except for carrying VLAN information between switches, and get ignored if presented on non-trunk ports.
But when Taylor used two switches, he could force packets to hop VLANs under certain conditions. Just as in the early example from Cisco documentation, the MAC addresses of the target system had to be known in advance. The other key condition was that the initiating system, the "attacker", must belong to the same VLAN as the trunk used to connect the switches. In Taylor's first attempt, the attacker and the trunk were both in VLAN one, and the target in VLAN two.
Subsequent investigation by a Cisco employee (you can find this at http://online.securityfocus.com/archive/1/27062) pointed out that this behaviour was not only supported by the 802.1Q standard, but also worked on other, non-Cisco, switches as well.
You can easily prevent VLAN hopping by configuring trunk ports so that their native VLANs do not match the VID of any other VLANs that you have configured. Remember that by default, the native VLAN for a trunk will be VID one, the default for any VLAN. You can choose to set the native VLAN for trunks to be 1001, or any value that your switch supports and is not used for any other VLAN.
FIREWALLS AND VLANS
Now that I have discussed how switches share VLAN information, we can examine firewalls that support VLAN-related policy. Firewalls get packets from VLAN-supporting switches complete with 802.1Q tags in their headers. Although I have only mentioned Ethernet in examples, 802.1Q tagging also applies to other network media, such as ATM and FDDI. What the VLAN-aware firewall can do is extract the tags and use the information within the tags to make policy-based security decisions.
802.1Q tags do not provide authentication. Tags just provide a form of identification, added by switches, that a particular packet came from a particular VLAN. That a firewall would act on this information is no more ridiculous than acting on the source address of a packet, as IP source addresses are also an unauthenticated means of identification--and one that can be spoofed.
Spoofing IP source addresses has been done for many years, and spoofing VLAN tags can be done as well. The most recent Linux operating systems (kernels in the 2.4 vintage) include support for acting as VLAN switches, and can generate any VLAN tag that the local system administrator chooses. Other software exists for spoofing VLAN tags. Taylor used the Network Associates' Sniffer Pro v.2.0.01 to generate packets, and this can be done in software as well.
The key to safely using 802.1Q tags for policy decisions is to design a network where switch trunks get connected to the firewall interface where decisions will be made based on VLAN tags. If there are other routes to this firewall interface, the possibility that packets with spoofed VLAN tags increases. The switches themselves must be properly configured, with trunk ports specifically configured for trunking, and added to a non-default VID.
Implicit in any discussion of switches is protecting administrative access to the switches themselves. Switches and other network equipment typically expose three different means for administrative access: telnet, HTTP, and SNMP. You should always disable methods of administrative access that you don't use, as well as adding access control to the methods that you do use. While the firewall can control access to switches when the source of an attempt is external, the firewall can do nothing about an internal attacker--or one that has gained access to an internal system.
Switches were not designed as security devices. Their use as such simply evolved over time, and is ancillary to their main use as devices that improve network performance. If you use a switch for security reasons, you are relying on the correct configuration of the switch, including understanding not only the standards that the switch software is based upon, but also the correct implementation of those standards. The 802.1Q spec itself is 211 pages long, and is only one of a handful of standards that a compliant switch manufacturer must support.
Any time that you need to segregate networks for serious security purposes, I recommend that you not use a switch.
CCNA VLan Basic knowledge
What is a VLAN?
To refresh your memory, a Local Area Network (LAN) is a set of connected devices like computers, hubs, and switches sharing the same pool of logical address space. Normally, a router is required to route packets from one LAN to another LAN. Traditionally, all packets within a LAN are broadcast to all other devices connected to that particular LAN.
As a result, a traditional LAN has several disadvantages as below:
* Usable bandwidth is shared among all the devices connected to the LAN
* ALL devices connected within a LAN can hear ALL the packets irrespective of whether the packet is meant for that device or not. It is possible for some unscrupulous node listening to data packets not meant for that.
* Suppose, your organization has different departments. Using a traditional LAN, when any changes take place within the organization, physical cables and devices need to be moved to reorganize the LAN infrastructure.
* A LAN cannot extend beyond its physical boundary across a WAN as in VLANs.
If you are looking for a simple networked solution for a small office, it may be a good idea to have a traditional LAN setup with a few hubs or switches. However, if you are planning for a large building or campus wide LAN for several individual departments, a VLAN is almost essential.
Virtual LANs (VLANs) can be considered as an intelligent LAN consisting of different physical LAN segments enabling them to communicate with each other as if they were all on the same physical LAN segment.
Benefits of VLAN: Several of the disadvantages of traditional LANs can be eliminated with the implementation of VLANs.
1. Improved Performance: In a traditional LAN, all the hosts within the LAN receive broadcasts, and contend for available bandwidth. As a result, the bandwidth is shared among all the connected devices within the LAN segment. If you are running high-bandwidth consumption applications such as groupware or server forms, a threshold point may easily be reached. After a threshold, the users may find the LAN too slow or un-responsive. With the use of VLAN, you can divide the big LAN into several smaller VLANs. For example, if there are two file servers, each operating at 100Mbps, in a traditional LAN both the servers have to share the LAN bandwidth of 100Mbps. If you put both the servers in separate VLANs, then both have an available bandwidth of 100Mbps each. Here the available bandwidth has been doubled.
2. Functional separation of an institute or a company: It is often required to separate the functional groups within a company or institute. For example, it might be necessary to separate HR department LAN from that of Production LAN. Traditionally, it requires a router to separate two physical LANs. However, you can set up two VLANs, one for Finance, and the other for Production without a router. A switch can route frames from one VLAN to another VLAN. With VLAN's it is easier to place a workgroup together eventhough they are physically in different buildings. In this case Finance VLAN does not forward packets to Production VLAN, providing additional security.
3. Ease of Network Maintenance:
Network maintenance include addition, removal, and changing the network users. With traditional LANs, when ever a User moves, it may be necessary to re-configure the user work station, router, and the servers. Some times, it may also be necessary to lay the cable, or reconfigure hubs and switches. If you are using VLANs, many of these reconfiguration tasks become unnecessary. For example, you can avoid network address configuration on the work station and the corresponding router if you use VLAN. This is because, routing traffic within VLANs doesn't require a router.
However, VLAN's add some administrative complexity, since the administration needs to manage virtual workgroups using VLANs.
4. Reduced Cost
VLANs minimize the network administration by way of reduced maintenance on account of workstation addition/deletion/changes. This in turn reduce the costs associated with LAN maintenance.
5. Security
Using a LAN, all work stations within the LAN get the frames meant for all other work stations within the broadcast domain. Since a VLAN splits the broadcast domain into two or more, it is possible to put work stations sharing sensitive data in one VLAN, and other work station in another VLAN. Of course, if two VLANs are not sufficient, you can split the work stations into as many VLANs as required. VLAN's can also be used to set up firewalls, restrict access, and send any intrusion alerts to the administrator.
Wednesday, October 15, 2008
CCNA 3 Ch 1 Lab Intro using Packet Tracer 5.0
Packet Tracer 5.0 is the latest version of Cisco Networking Academy’s comprehensive networking technology teaching and learning software. Innovative features of Packet Tracer 5.0, including powerful simulation, visualization, authoring, assessment, and collaboration capabilities, will help students and teachers collaborate, solve problems, and learn concepts in an engaging and dynamic social environment.
Packet Tracer makes both teaching and learning easier - instructors and students can create their own virtual “network worlds” for exploration, experimentation, and explanation of networking concepts and technologies.
* Instructors can demonstrate technologies and configurations using Packet Tracer to teach complex CCNA-level networking concepts, making it extremely useful for lectures, group and individual labs, assessments, troubleshooting and modeling tasks, homework, games, and competitions.
* Students can design, configure and troubleshoot networks using Packet Tracer’s versatile simulation and visualization environment, which also provides the opportunity and flexibility for additional practice outside of the classroom environment.
Packet Tracer supplements classroom equipment and provides students complementary learning opportunities that are not physically possible to create in the classroom or lab. In addition, Packet Tracer supplements the CCNA curricula and Packet Tracer activities are integrated throughout both CCNA Discovery and CCNA Exploration to provide rich networking technology learning experiences.
Packet Tracer 5.0 offers a unique combination of realistic simulation and visualization experiences, complex assessment and activity authoring capabilities, and opportunities for multiuser collaboration and competition, and is available free of charge to all Networking Academy instructors, students, and alumni. Visit the Packet Tracer 5.0 resource page on Academy Connection today to download this free software and explore the new possibilities in networking education.
Saturday, October 11, 2008
ESwitching Chapter 6 - CCNA Exploration: LAN Switching and Wireless (Version 4.0) - Question and Answer
With answer
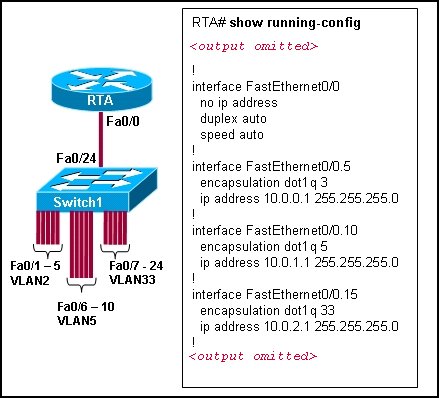
Refer to the exhibit. Switch1 is correctly configured for the VLANs that are displayed in the graphic. The configuration that is shown was applied to RTA to allow for interVLAN connectivity between hosts attached to Switch1. After testing the network, the administrator logged the following report:
Hosts within each VLAN can communicate with each other.
Hosts in VLAN5 and VLAN33 are able to communicate with each other.
Hosts connected to Fa0/1 through Fa0/5 do not have connectivity to host in other VLANs.
Why are hosts connected to Fa0/1 through Fa0/5 unable to communicate with hosts in different VLANs?
The router interface is shut down.
The VLAN IDs do not match the subinterface numbers.
All of the subinterface addresses on the router are in the same subnet.
The router was not configured to forward traffic for VLAN2.
The physical interface, FastEthernet0/0, was not configured with an IP address.
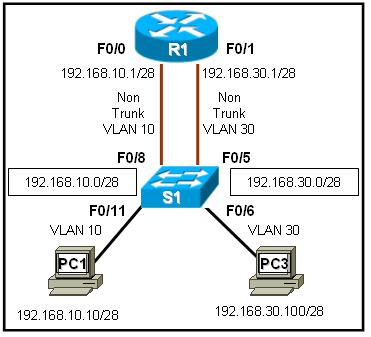
Refer to the exhibit. R1 is routing between networks 192.168.10.0/28 and 192.168.30.0/28. PC1 can ping R1 interface F0/1, but cannot ping PC3. What is causing this failure?
PC1 and PC3 are not in the same VLAN.
The PC3 network address configuration is incorrect.
The S1 interface F0/11 should be assigned to VLAN30.
The F0/0 and F0/1 interfaces on R1 must be configured as trunks.
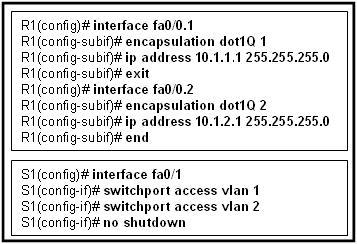
Refer to the exhibit. Port Fa0/0 on router R1 is connected to port Fa0/1 on switch S1. After the commands shown are entered on both devices, the network administrator determines that the devices on VLAN 2 are unable to ping the devices on VLAN 1. What is the likely problem?
R1 is configured for router-on-a-stick, but S1 is not configured for trunking.
R1 does not have the VLANs entered in the VLAN database.
Spanning Tree Protocol is blocking port Fa0/0 on R1.
The subinterfaces on R1 have not been brought up with the no shutdown command yet.
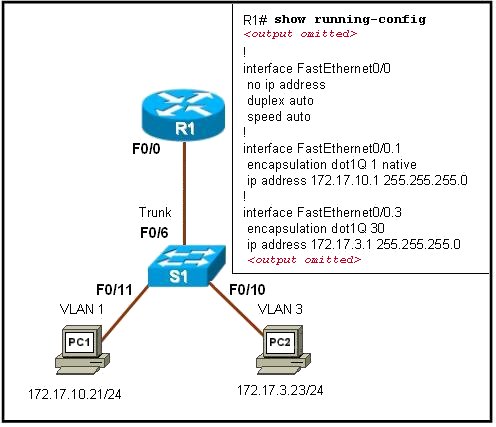
Refer to the exhibit. PC1 has attempted to ping PC2 but has been unsuccessful. What could account for this failure?
PC1 and R1 interface F0/0.1 are on different subnets.
The encapsulation is missing on the R1 interface F0/0.
An IP address has not been assigned to the R1 physical interface.
The encapsulation command on the R1 F0/0.3 interface is incorrect.
5. A router has two FastEthernet interfaces and needs to connect to four VLANs in the local network. How can this be accomplished using the fewest number of physical interfaces without unnecessarily decreasing network performance?
Implement a router-on-a-stick configuration.
Add a second router to handle the inter-VLAN traffic.
Use a hub to connect the four VLANS with a FastEthernet interface on the router.
Interconnect the VLANs via the two additional FastEthernet interfaces.

Refer to the exhibit. Which three statements describe the network design shown in the exhibit? (Choose three.)
This design will not scale easily.
The router merges the VLANs into a single broadcast domain.
This design uses more switch and router ports than are necessary.
This design exceeds the maximum number of VLANs that can be attached to a switch.
This design requires the use of the ISL or 802.1q protocol on the links between the switch and the router.
If the physical interfaces between the switch and router are operational, the devices on the different VLANs can communicate through the router.
7. In which situation could individual router physical interfaces be used for InterVLAN routing, instead of a router-on-a-stick configuration?
a network with more than 100 subnetworks
a network with a limited number of VLANs
a network with experienced support personnel
a network using a router with one LAN interface
8. What distinguishes traditional routing from router-on-a-stick?
Traditional routing is only able to use a single switch interface. Router-on-a-stick can use multiple switch interfaces.
Traditional routing requires a routing protocol. Router-on-a-stick only needs to route directly connected networks.
Traditional routing uses one port per logical network. Router-on-a-stick uses subinterfaces to connect multiple logical networks to a single router port.
Traditional routing uses multiple paths to the router and therefore requires STP. Router-on-a-stick does not provide multiple connections and therefore eliminates the need for STP.
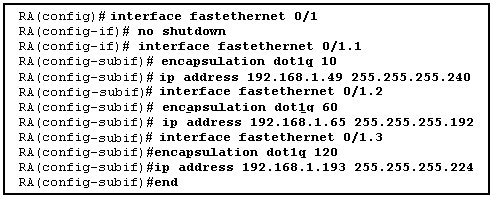
Refer to the exhibit. The commands for a router to connect to a trunked uplink are shown in the exhibit. A packet is received from IP address 192.168.1.54. The packet destination address is 192.168.1.120. What will the router do with this packet?
The router will forward the packet out interface FastEthernet 0/1.1 tagged for VLAN 10.
The router will forward the packet out interface FastEthernet 0/1.2 tagged for VLAN 60.
The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 120.
The router will not process the packet since the source and destination are on the same subnet.
The router will drop the packet since no network that includes the source address is attached to the router.
10. Which three elements must be used when configuring a router interface for VLAN trunking? (Choose three.)
one subinterface per VLAN
one physical interface for each subinterface
one IP network or subnetwork for each subinterface
one trunked link per VLAN
a management domain for each subinterface
a compatible trunking protocol encapsulation for each subinterface
11. What are the steps which must be completed in order to enable inter-VLAN routing using router-on-a-stick?
Configure the physical interfaces on the router and enable a routing protocol.
Create the VLANs on the router and define the port membership assignments on the switch.
Create the VLANs on the switch to include port membership assignment and enable a routing protocol on the router.
Create the VLANs on the switch to include port membership assignment and configure subinterfaces on the router matching the VLANs.
12. What two statements are true regarding the use of subinterfaces for inter-VLAN routing? (Choose two.)
subinterfaces have no contention for bandwidth
more switch ports required than in traditional inter-VLAN routing
fewer router ports required than in traditional inter-VLAN routing
simpler Layer 3 troubleshooting than with traditional inter-VLAN routing
less complex physical connection than in traditional inter-VLAN routing

Refer to the exhibit. All devices are configured as shown in the exhibit. PC2 can successfully ping the F0/0 interface on R1. PC2 cannot ping PC1. What might be the reason for this failure?
R1 interface F0/1 has not been configured for subinterface operation.
S1 interface F0/6 needs to be configured for operation in VLAN10.
S1 interface F0/8 is in the wrong VLAN.
S1 port F0/6 is not in VLAN10.
14. What is important to consider while configuring the subinterfaces of a router when implementing inter-VLAN routing?
The physical interface must have an IP address configured.
The subinterface numbers must match the VLAN ID number.
The no shutdown command must be given on each subinterface.
The IP address of each subinterface must be the default gateway address for each VLAN subnet
15.
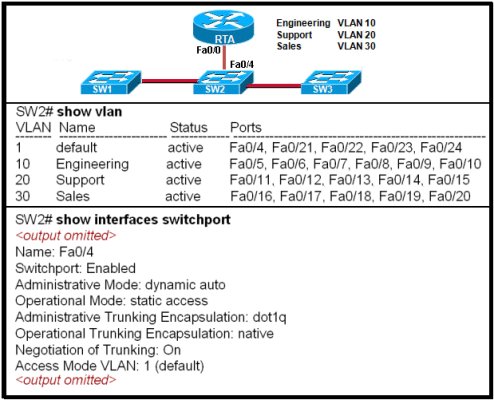
Refer to the exhibit. The network administrator correctly configures RTA to perform inter-VLAN routing. The administrator connects RTA to port 0/4 on SW2, but inter-VLAN routing does not work. What could be the possible cause of the problem with the SW2 configuration?
Port 0/4 is not active.
Port 0/4 is not a member of VLAN1.
Port 0/4 is configured in access mode.
Port 0/4 is using the wrong trunking protocol.

Refer to the exhibit. What two conclusions can be drawn from the output that is shown? (Choose two.)
The no shutdown command has not been issued on the FastEthernet 0/0 interface.
Both of the directly connected routes that are shown will share the same physical interface of the router.
A routing protocol must be configured on the network in order for the inter-VLAN routing to be successful.
Inter-VLAN routing between hosts on the 172.17.10.0/24 and 172.17.30.0/24 networks is successful on this network.
Hosts in this network must be configured with the IP address that is assigned to the router physical interface as their default gateway.
17. Devices on the network are connected to a 24-port Layer 2 switch that is configured with VLANs. Switch ports 0/2 to 0/4 are assigned to VLAN 10. Ports 0/5 to 0/8 are assigned to VLAN 20, and ports 0/9 to 0/12 are assigned to VLAN 30. All other ports are assigned to the default VLAN. Which solution allows all VLANs to communicate between each other while minimizing the number of ports necessary to connect the VLANs?
Configure ports 0/13 to 0/16 with the appropriate IP addresses to perform routing between VLANs.
Add a router to the topology and configure one FastEthernet interface on the router with multiple subinterfaces for VLANs 1, 10, 20, and 30.
Obtain a router with multiple LAN interfaces and configure each interface for a separate subnet, thereby allowing communication between VLANs.
Obtain a Layer 3 switch and configure a trunk link between the switch and router, and configure the router physical interface with an IP address on the native VLAN.
18. Which statement is true about ARP when inter-VLAN routing is being used on the network?
When router-on-a-stick inter-VLAN routing is in use, each subinterface has a separate MAC address to send in response to ARP requests.
When VLANs are in use, the switch responds to ARP requests with the MAC address of the port to which the PC is connected.
When router-on-a-stick inter-VLAN routing is in use, the router returns the MAC address of the physical interface in response to ARP requests.
When traditional inter-VLAN routing is in use, devices on all VLANs use the same physical router interface as their source of proxy ARP responses.
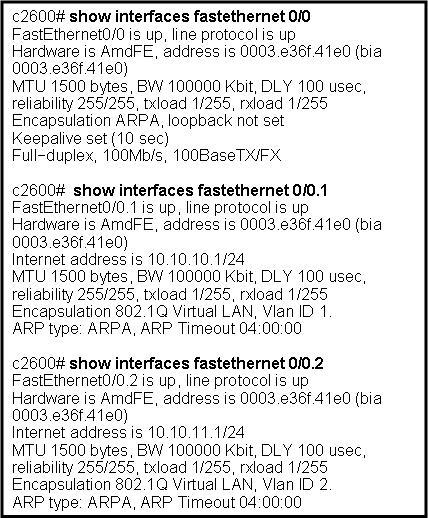
Refer to the exhibit. Which two statements are true about the operation of the subinterfaces? (Choose two.)
Incoming traffic that has a VLAN ID of 2 is processed by subinterface fa0/0.2.
Incoming traffic with VLAN ID 0 is processed by interface fa0/0.
Subinterfaces use unique MAC addresses by adding the 802.1Q VLAN ID to the hardware address.
Traffic inbound on this router is processed by different subinterfaces, depending on the VLAN from which the traffic originated.
Reliability of both subinterfaces is poor because ARP is timing out.
Both subinterfaces remain up with line protocol up, even if fa0/0 line protocol is down.
20. Which two statements are true about the interface fa0/0.10 command? (Choose two.)
The command applies VLAN 10 to router interface fa0/0.
The command is used in the configuration of router-on-a-stick inter-VLAN routing.
The command configures a subinterface.
The command configures interface fa0/0 as a trunk link.
Because the IP address is applied to the physical interface, the command does not include an IP address
Thursday, October 9, 2008
Troubleshooting Ipconfig
An error occurred while renewing interface
Can ping ip but not name
Can ping IP but not hostname after installed/upgraded software
Can receive IP packets but not send them
Can't obtain/renew IP addresses from the DHCP server
Can't ping my own IP address
Cannot use the 2nd NIC
IP address conflicts
No IP while the network cable is disconnected
No operation can be performed on the adapter
One-way ping only
Some Win9x obtain different subnet mask
The DHCP client has obtained an IP address that is already in use on the network
Unexpected network failure or insufficient access or access is denied
Why the ipconfig shows 0.0.0.0 ip even you have assigned a static ip
Why do I get 169.254.x.x IP?
An error occurred while renewing interface
Symptoms: When trying to release and renew the IP address using the Ipconfig command, you may receive the following error message: “An error occurred while renewing interface 'Internet': An operation was attempted on something that is not a socket.”
Cause: These issues may occur if the Winsock registry keys are damaged or corrupted.
Can ping ip but not name
I have a situation here where I could ping an IP of a computer but how come I couldn't ping with its computer name?
1. Incorrect WINS and DNS settings.
2. Incorrect TCP/IP settings
3. Check lmhosts and hosts files
Can ping IP but not hostname after installed/upgraded software
Cause: the may modify the networking configuration in registry.
Can receive IP packets but not send them
Symptoms: When using ipconfig command, you may have no IP address or no Automatic Private IP Addressing (APIPA) address. You may be receiving IP packets but not sending them.
Cause: These issues may occur if the Winsock registry keys are damaged or corrupted.
Can't ping my own IP address
Failure to ping a computer's own IP address is most likely caused by a firewall program or improperly configured.
Can't obtain/renew IP addresses from the DHCP server
Symptoms: 1) you have a DHCP client which may not be able to obtain/renew IP addresses from the DHCP server intermittently. 2) after setup a workstation to obtain an IP address from DHCP, the machine can't ping others and ipconfig /all shows Autoconfiguration IP Address. . . : 169.254.x.x.
Resolutions: 1) If this is XP, obtain the latest service pack for Windows XP.
2) Use the Network Diagnostics tool to identify any failed settings. To do this, go to Help and Support>Use Tools to view your computer information and diagnose problems>Network Diagnostics>Scan your system. When the process finishes, check for any items marked "FAILED" in red, expand those categories, and view the additional details about what the testing showed.
3) Assign a static ip on the client and ping the DHCP server. If you can't ping the DHCP server, check the connection and hardware.
4) If you can ping the DHCP after assigning static ip, check the DHCP settings.
5) Make sure no firewall is running on your LAN.
6) Run Repair this connection if it is XP. Or use netsh to reset TCP/IP configuration.
7) If it is win98/w2k, remove and reinstall TCP/IP.
8) Try to upgrade the new NIC driver.
9) Make sure you don't run out of IPs in the DHCP scope.
10) If you use a router as DHCP, you may want to upgrade the firmware.
Cannot use the 2nd NIC
Symptom: You have two computers and each one has two NICs. You are using the first NIC with 192.168.1.0/24 to connect the Internet and it works. You also want to use the 2nd NIC with crossover cable to connect to each other using the same IP range (one is 192.168.1.10 and another is 192.168.1.11). You can't ping each other (192.168.1.10 and 192.168.1.11).
Resolution: The 2nd NICs should use the different IP range.
IP address conflicts
SYMPTOMS: when trying to set the IP address on a NIC, you may receive the following error message: "The IP address XXX.XXX.XXX.XXX you have entered for this network adapter is already assigned to another adapter Name of adapter. Name of adapter is hidden from the network and Dial-up Connections folder because it is not physically in the computer or is a legacy adapter that is not working. If the same address is assigned to both adapters and they become active, only one of them will use this address. This may result in incorrect system configuration. Do you want to enter a different IP address for this adapter in the list of IP addresses in the advanced dialog box? "
RESOLUTION:
1. If you click Yes, you see the TCP/IP properties where you can change the IP address. Then assign the different IP.
2. If you click No, the IP address is assigned to the network adapter. To resolve this problem, uninstall the ghosted network adapter from the registry: At command prompt, type set devmgr_show_nonpresent_devices=1, and then press ENTER. Type Start DEVMGMT.MSC, and then press ENTER. Click View, and then click Show Hidden Devices. Expand the Network Adapters tree and right-click the dimmed network adapter, and then click Uninstall.
No IP while the network cable is disconnected
Symptoms: your computer has a static IP. However, the ipconfig shows no IP (Media State - Cable Disconnected) while the network cable is disconnected.
Cause: this is by design. If you have some software using TCP/IP whiteout connecting to a network, you may setup it manually.
No operation can be performed on the adapter
Symptoms: when attempting to use ipconfig /release or renew command, you get "No operation can be performed on the adapter
Causes: 1. The network is up-plugged or no NIC. 2. You are using static IP.
One-way ping only
If you can ping other computers and other computers can't ping your computer, this is often caused by an improperly configured firewall
on you computer. For example, ICF should not be enabled on LAN NIC.
Some Win9x obtain different subnet mask
Symptoms: In your domain network, some computers (most are win9x) obtain mask 255.255.255.0 instead of 255.0.0.0 randomly and they can't logon to the Domain. IPCONFIG /renew doesn't fix the problem. If you assign static ip and correct mask, the computer will be able to logon without any problem. If you check the WINS, you may find many bad records.
Possible reasons: you may have another network device (possible a router) except main DHCP functions as a DHCP.
The DHCP client has obtained an IP address that is already in use on the network
Symptom: When trying to renew IP, you may get this error "An error occurred while renewing the interface Local Area Connection: The
DHCP client has obtained an IP address that is already in use on the network. The local interface will be disabled until the DHCP client can obtain a new address."
Resolution: 1. Release and the renew it.
2. Clean the internal DNS and WINS records.
Refer to case 083104LR
Unexpected network failure or insufficient access or access is denied
Symptoms: when trying to use ipconfig /release or renew, you may receive the following message "The following error occurred when releasing adapter Local Area Connection: Unexpected network failure or insufficient access or access is denied"
Cause: You don't have permission to release or renew the IP.
Why do I get 169.254.x.x IP?
Symptom: The Internet Assigned Numbers Authority (IANA) has reserved 169.254.0.0-169.254.255.255 for Automatic Private IP Addressing. If the computer can't get ip from DHCP, APIPA provides an address that is guaranteed not to conflict with routable addresses.
Resolutions: 1) Make sure you have good connection.
2) Check the hardware and settings.
3) Make sure the DHCP is working.
4) For the test, you can assign static ip. If static ip works, it is possible DHCP issue. If static ip doesn't work, check the hardware or connection.
5) WinSock2 stack may be corrupted and need to repair.
Why the ipconfig shows 0.0.0.0 ip even you have assigned a static ip
Question: I have assigned a static ip, subnet to the computer, but the ipconfig shows IP address is 0.0.0.0 and subnet mask 0.0.0.0.. Why?
Answer: An existing IP address on the network has the same IP address. You may use tracert ip, WINS and DNS records to find out another computer using the same IP.
If your laptop users frequently disconnect from one network segment and reconnect to another network segment, they may not be able to access the second network. Resolution will be run ipconfig /registerdns.
Common commands you should master when working with the Cisco IOS
#1: The “?”
It may seem entirely too obvious that you should know how to type ? to ask for help when using the Cisco IOS. However, the Cisco IOS is completely different from other operating systems when it comes to using the question mark (help key). As the IOS is a command-line operating system with thousands of possible commands and parameters, using the ? can save your day.
You can use the command in many ways. First, use it when you don’t know what command to type. For example, type ? at the command line for a list of all possible commands. You can also use ? when you don’t know what a command’s next parameter should be. For example, you might type show ip ? If the router requires no other parameters for the command, the router will offer CR as the only option. Finally, use ? to see all commands that start with a particular letter. For example, show c? will return a list of commands that start with the letter c.
#2: show running-configuration
The show running-config command shows the router, switch, or firewall’s current configuration. The running-configuration is the config that is in the router’s memory. You change this config when you make changes to the router. Keep in mind that config is not saved until you do a copy running-configuration startup-configuration. This command can be abbreviated sh run.
#3: copy running-configuration startup-configuration
This command will save the configuration that is currently being modified (in RAM), also known as the running-configuration, to the nonvolatile RAM (NVRAM). If the power is lost, the NVRAM will preserve this configuration. In other words, if you edit the router’s configuration, don’t use this command and reboot the router–those changes will be lost. This command can be abbreviated copy run start. The copy command can also be used to copy the running or startup configuration from the router to a TFTP server in case something happens to the router.
#4: show interface
The show interface command displays the status of the router’s interfaces. Among other things, this output provides the following:
* Interface status (up/down)
* Protocol status on the interface
* Utilization
* Errors
* MTU
This command is essential for troubleshooting a router or switch. It can also be used by specifying a certain interface, like shint fa0/0.
#5: show ip interface
Even more popular than show interface are show ip interface and show ip interface brief. The show ip interface command provides tons of useful information about the configuration and status of the IP protocol and its services, on all interfaces. The show ip interface brief command provides a quick status of the interfaces on the router, including their IP address, Layer 2 status, and Layer 3 status.
#6: config terminal, enable, interface, and router
Cisco routers have different modes where only certain things can be shown or certain things can be changed. Being able to move between these modes is critical to successfully configuring the router.
For example, when logging in, you start off at the user mode (where the prompt looks like >). From there, you type enable to move to privileged mode (where the prompt looks like #). In privileged mode, you can show anything but not make changes. Next, type config terminal (or config t) to go to global configuration mode (where the prompt looks like router(config)# ). From here, you can change global parameters. To change a parameter on an interface (like the IP address), go to interface configuration mode with the interface command (where the prompt looks like router(config-if)#). Also from the global configuration mode, you can go into router configuration using the router {protocol} command. To exit from a mode, type exit.
#7: no shutdown
The no shutdown command enables an interface (brings it up). This command must be used in interface configuration mode. It is useful for new interfaces and for troubleshooting. When you’re having trouble with an interface, you may want to try a shut and no shut. Of course, to bring the interface down, reverse the command and just say shutdown. This command can be abbreviated no shut.
#8: show ip route
The show ip route command is used to show the router’s routing table. This is the list of all networks that the router can reach, their metric (the router’s preference for them), and how to get there. This command can be abbreviated shipro and can have parameters after it, like shiproospf for all OSPF routers. To clear the routing table of all routes, you do clear ip route *. To clear it of just one route, do clear ip route 1.1.1.1 for clearing out that particular network.
#9: show version
The show version command gives you the router’s configuration register (essentially, the router’s firmware settings for booting up), the last time the router was booted, the version of the IOS, the name of the IOS file, the model of the router, and the router’s amount of RAM and Flash. This command can be abbreviated shver.
#10: debug
The debug command has many options and does not work by itself. It provides detailed debugging output on a certain application, protocol, or service. For example, debug ip route will tell you every time a router is added to or removed from the router.
Mitigate problems using Cisco IOS debug
This article is intended for the intermediate level network administrator who has never encountered circumstances that would require debugging the Cisco IOS. But if you've used debug before, perhaps this article will give you some suggestions for ways to use debug that you haven't previously tried.
Key points
Before I introduce 10 ways to use Cisco IOS debug, here are a few tips and caveats:
- · The techniques I'm including are not the only ways to use debug. In fact, there are hundreds of ways to use debug. Listing A: shows all the possible subcommands that can be debugged in IOS 12.2 (the version I was running). You will see that there are more than you would ever want to use. In addition, each subcommand has its own subcommands. I'll be focusing on some of the debug commands I consider most common and useful.
- · Using Cisco IOS debug can be dangerous and should first be used on a test router and then used carefully on a production router. I don’t want anyone to get fired because he crashed the company’s production router after trying debug commands from this article.
- · By default, debug messages will go to the console and will not be sent to any log. To log debug output (or any system output) to the IOS system log, you must turn on logging buffered in global configuration mode. You can see if logging is on by issuing the show logging command on your router. The output looks like Listing B. As you can see, there are three kinds of logging: console, monitor, and buffer. There are also different levels of logging.
- · If you want to see debug output on a terminal (or Telnet session) that is not the console, use the terminal monitor command.
- · You can also set up “conditional debugging” to debug only when certain conditions apply. See Cisco's Troubleshooting and Fault Management to learn more about this.
- · If you turn on some debugging that is filling up your screen, the quickest way to turn it off is by running the un all command. The un is a built-in macro for undebug.
Now let’s move on and look at 10 ways to use Cisco IOS debug. We'll start with number 10 and work our way up to the most useful debug command.
10. Debug all
By far, the most dangerous debug command is debug all. This command will most likely crash a production router. The Cisco IOS is nice enough to ask, “Are you sure?” before doing it. Only use this command if you are desperate, you know you are on a test router, and/or you are having trouble isolating the proper subcommand to debug. To satisfy your curiosity of what it looks like to run it, Listing C shows the output from executing the command and then issuing show debug to see what it turned on.
9. Debug with ISDN and dialer
Debugging is helpful when troubleshooting Cisco router dialup configurations. In my experience, these technologies rarely seem to work the first time. The best way to configure IOS dialup technologies (or any networking technologies) is layer by layer, testing each layer after configuring it. I try to think of a multilayer cake, where the icing is the successful testing of each OSI layer after each configuration. When something doesn’t work, debug is usually a must. Useful debug commands for ISDN and dialup networking appear below:
- · debug isdn events debugs all ISDN events. Start with this one first before trying q921 or q931, as those are very verbose and events may tell you all you need to know.
- · debug isdn q921 is Layer 2.
- · debug isdn q931 is Layer 3.
- · debug dialer events will tell you about the calls (i.e., the reason the call was initiated and/or disconnected). Here is some sample output:
00:18:52: BRI0/0 DDR: Attempting to dial 8358661
00:19:22: BRI0/0:2 DDR: disconnecting call
This can be especially helpful if you have a router that keeps calling when you don't want it to.
00:39:24: BRI0/0 DDR: ip (s=1.1.1.2, d=1.1.1.1), 100 bytes, outgoing interesting (ip PERMIT)
00:39:24: BRI0/0 DDR: ip (s=1.1.1.2, d=1.1.1.1), 100 bytes, outgoing interesting (ip PERMIT)
00:39:24: BRI0/0 DDR: ip (s=1.1.1.2, d=1.1.1.1), 100 bytes, outgoing interesting (ip PERMIT)
00:41:09: BRI0/0 DDR: cdp, 273 bytes, outgoing uninteresting (no list matched)
8. PPP authentication
If you configured PPP authentication on your dialup lines (which you should, for security reasons), you could end up with username/password mismatches on each side. Finding out that this is the reason that the line won’t come up can be impossible without using debug ppp authentication.
Here's some sample output of missing username/password information on one router:
00:32:30: BR0/0:1 CHAP: O CHALLENGE id 13 len 23 from "r2"
00:32:31: BR0/0:1 CHAP: I CHALLENGE id 2 len 23 from "r1"
00:32:31: BR0/0:1 CHAP: O RESPONSE id 2 len 23 from "r2"
00:32:31: BR0/0:1 CHAP: I FAILURE id 2 len 26 msg is "Authentication failure"
This is sample output of an incorrect password on one router:
00:47:05: BR0/0:1 CHAP: O CHALLENGE id 25 len 23 from "r2"
00:47:05: BR0/0:1 CHAP: I CHALLENGE id 19 len 23 from "r1"
00:47:05: BR0/0:1 CHAP: O RESPONSE id 19 len 23 from "r2"
00:47:05: BR0/0:1 CHAP: I FAILURE id 19 len 25 msg is "MD/DES compare failed"
7. Debug {topology} packet
As I mentioned above, it is best to troubleshoot networking technologies using a layered approach, working your way up the OSI model from Layer 1. (I give credit to Bruce Caslow and his book Cisco Certification: Bridges, Routers, and Switches for CCIEs for carefully documenting this approach.)
Using that model, for whatever network topology you are working with, you can use the debug command to see that your Layer 2 packets are being encapsulated properly. (Of course, I'm assuming that all the cables are connected at Layer 1.) For instance, let's say that you work with frame-relay and you're having trouble getting packets across a link. You've verified that the link is up, but there is still no data passing on it. You could try
debug frame-relay packet
Then, you could attempt to ping the interface on the remote router. If the ping passes, you will get the following:
01:03:22: Serial0/0:Encaps failed--no map entry link 7(IP)
This tells you that encapsulation failed for the IP packet into the frame-relay protocol. It even tells you that it failed because there is no frame-relay map statement. If you fix that and try it again, you might find that you get no frame-relay errors. But then the packet still may not pass. Thus, you'll need to go up to Layer 3 and try:
debug ip packet
You might get this output:
01:06:46: IP: s=1.1.1.2 (local), d=11.11.11.11, len 100, unroutable
This tells you that there is no IP route for your packet to traverse. Thus, you know you need to add a route.
You can insert whatever networking topology you are working with on the debug {topology} line. Some other possibilities are:
- · debug atm packet
- · debug serial packet
- · debug ppp packet
- · debug dialer packet
- · debug fastethernet packet
6. Debug crypto (IPSec and VPN features)
I won’t go into a lot of detail and examples here since IPSec and VPN are huge topics that can get very complex. But I do want to point out that you can troubleshoot IPSec connections with debugging commands. Because of the popularity of VPN and IPSec, it is important to know how to use debug commands for these technologies. Some of the possibilities are:
- · debug crypto isakmp
- · debug crypto ipsec
- · debug crypto engine
- · debug ip security
- · debug tunnel
In addition, debug ip packet, as mentioned below, is useful in troubleshooting IPsec connections.
If you want to learn more on this topic, I recommend going to Cisco’s IP Security Protocols Section, choosing the protocol you are interested in (IPSec, IKE, etc.), and looking at the different configurations along with their recommended troubleshooting methods.
5. Debug IP routing
Using debug with IP routing protocols can be useful as well. For example, to know if you have a route flapping (a route being added and removed frequently), you can use debug ip routing.
If you had a flapping route, you might see something like:
01:30:56: RT: add 111.111.111.111/32 via 12.12.12.11, ospf metric [110/65]
01:31:13: RT: del 111.111.111.111/32 via 12.12.12.11, ospf metric [110/65]
01:31:13: RT: delete subnet route to 111.111.111.111/32
01:31:13: RT: delete network route to 111.0.0.0
01:32:56: RT: add 111.111.111.111/32 via 12.12.12.11, ospf metric [110/65]
01:33:13: RT: del 111.111.111.111/32 via 12.12.12.11, ospf metric [110/65]
01:33:13: RT: delete subnet route to 111.111.111.111/32
01:33:13: RT: delete network route to 111.0.0.0
This could indicate a routing loop in your network. On the other hand, it could indicate a link going up and down, perhaps a bouncing dialup interface or frame-relay interface.
4. Debug ip {routing protocol}
You can insert many options with debug ip. Issuing the debug ip ? command will display them. We've included the options in Listing D.
Most routing protocols (e.g., OSPF, EIGRP, IGRP, and BGP) are included in this list. Each has its own extensive options that can be debugged. (You can see all the options for a particular protocol by issuing the debug ip {routing protocol} ? command.) For instance, the only way to know that your two OSPF routers are not forming an adjacency due to mismatched authentication types is to issue debug ip ospf adjacency.
You might see the following output, telling you that the authentication types are mismatched:
01:39:46: OSPF: Rcv pkt from 12.12.12.11, Serial0/0 : Mismatch Authentication type. Input packet specified type 0, we use type 2
In this case, if it weren't for debug, you could be scratching your head for a while.
3. Debug list
An interesting debug command that isn’t widely known is debug list. This command doesn’t actually debug anything. Instead, it sets an interface and/or access list for the next debug you enter. So if you are going to issue some command that you know will produce a lot of output but that doesn’t have an option to limit that output with an access command, you can first issue the debug list XXX command (where XXX is an access list number you have already created) and then run the command you want to debug on. An example would be:
debug list 1
debug dhcp detail
DHCP client activity debugging is on for access list: 1 (detailed)
2. Log an access list to system or syslog
You can use the log option at the end of an access list to log packets that are permitted or denied. This could enable you to log packets that are denied on a router being used as a firewall or to control access at an important network point. Remember that a firewall doesn’t have to just protect you from the Internet; it can protect higher security departments (such as accounting), be placed between two business partners, or just keep some traffic (like P2P traffic) off your network. While this isn’t technically a debug command, it can certainly be used for debugging and troubleshooting. Let's look at a couple of examples.
First, suppose that you want to allow only BGP traffic in your network and keep track of all other traffic that attempts to enter a link. Here's a sample configuration:
Interface Serial 0/0
Access-group 100 in
access-list 100 remark Begin -- Allow BGP IN and OUT
access-list 100 permit tcp host 1.1.1.1 host 2.2.2.2 eq bgp
access-list 100 permit udp any host 2.2.2.2 gt 33000
access-list 100 remark End
access-list 100 deny ip any any log
All traffic will go to your Cisco router’s log if you have “logging buffered” turned on or to a syslog server if you configured one.
For the second example, let's say you are trying to nail down an access list to permit only the proper traffic to go over your dialup link. You use an access list and log the existing traffic to get an idea of what is being carried so that you can configure the correct access list. Here's a sample configuration:
Interface BRI 0/0
Access-group 100 in
Access-group 100 out
access-list 100 permit ip any any log
If you look at the output in the router’s log, you will see that an ICMP packet and a TCP packet went across your link:
02:03:43: %SEC-6-IPACCESSLOGDP: list 100 permitted icmp 1.1.1.2 -> 1.1.1.1 (0/0), 1 packet
02:06:25: %SEC-6-IPACCESSLOGP: list 100 permitted tcp 1.1.1.2(0) -> 1.1.1.1(0), 1 packet
1. Debug IP packet detail XXX (access list number)
My number-one debug technique is using an access list to see all the traffic going to and from some destination, just like a basic sniffer/protocol analyzer. The limitation to this one is that you can’t see the packet payload and can see almost nothing of the headers.
Since you can do this with an access list, you can nail it down to a particular host, protocol, port, or network range, as well as using a uni- or bi-directional access list. I know it isn’t a real protocol analyzer, but it could still come in handy—and it's already built into the IOS. The sample configuration below shows the logging of all Telnet packets to your router. (These could just as well be a host on one of your router’s networks.)
access-list 101 permit tcp any any eq telnet
debug ip packet detail 101
IP packet debugging is on (detailed) for access list 101
Listing Eshows the sample output of what the debug output would look like.
You can see from the output that you get the IP source, destination, interfaces, source and destination port numbers, sequence numbers, acknowledgement numbers, window sizes, and TCP communication flags (SYN, ACK, FIN).
Troubleshoot Cisco routers and switches using the debug commands - Part 3
What are the three most common mistakes made when using Debug?
Using Debug can be a risky proposition, and even experienced admins have made mistakes when using it.
I’d say the number one common mistake is to forget that you have left Debug on in a production environment. Sometimes, we get so focused on resolving the issue that when we get it resolved, we are on to the next “opportunity” and forget to issue the no debug command to turn off debugging. I think that many a network admin can attest to horror stories of when they brought their router to its knees because they forgot this simple task of turning off Debug.
The second common mistake would be not realizing the effect on your router of issuing a lot of Debug commands at the same time. Remember that the router’s job is to forward packets, not to monitor processes and generate Debug messages. For example, you are having a problem with the packets on your router, so you issue the Debug statement debug ip packet. Then you decide that you want to view the events on the RIP protocol. Now, you have two separate Debug statements that are being processed and sent to the console. Debug statements are processed at a higher priority than other network traffic, so, needless to say, these Debug statements can jeopardize your router’s performance.
The third common mistake made with the Debug command is entering debug all or debug ip packet detail on a production router. Either one of these commands can crash a heavily loaded production router. Luckily, there is an “are you sure” prompt before these take effect; however, that hasn’t prevented every debug-related catastrophe. You should be as specific as possible when using Debug, and then turn it off as quickly as possible. Also, always test your Debug commands on a test router before using them in a production environment.
Troubleshoot Cisco routers and switches using the debug commands - Part 2
Let’s take a look at a simple example. We are going to view RIP (Routing Information Protocol) in Debug mode.
Router# debug ip RIP
RIP protocol debugging is on
To verify what debugging is enabled, use this command:
Router# show debug
RIP protocol debugging is on
The output from whatever type of debug is enabled will be sent to wherever the Cisco IOS logging system tells that output to go. Either you will receive the output on your screen, it will go to the buffered log on the router, or it will go to a syslog server across the network (or all of these).
To see what level the various outputs are set to and where the output will go, type:
Router# show logging
Syslog logging: enabled (1 messages dropped, 3 messages rate-limited,
0 flushes, 0 overruns, xml disabled, filtering disabled)
Console logging: level debugging, 8 messages logged, xml disabled,
filtering disabled
Monitor logging: level debugging, 0 messages logged, xml disabled,
filtering disabled
Buffer logging: level warnings, 2 messages logged, xml disabled,
filtering disabled
Logging Exception size (4096 bytes)
Count and timestamp logging messages: disabled
Trap logging: level informational, 12 message lines logged
Log Buffer (51200 bytes):
*Jun 9 20:56:49.195: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Jun 9 20:56:49.231: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up
Router#
The console should display RIP updates that are sent and received through the RIP protocol. Here is an example of what you might see for RIP debugging:
*Jun 9 21:13:56.471: RIP: sending v1 update to 255.255.255.255 via FastEthernet0/0 (1.1.1.1)
*Jun 9 21:13:56.471: RIP: build update entries - suppressing null update
*Jun 9 21:14:22.519: RIP: sending v1 update to 255.255.255.255 via FastEthernet0/0 (1.1.1.1)
*Jun 9 21:14:22.519: RIP: build update entries - suppressing null update
Remember that you should use Debug only for a short time to get a snippet of information, and then turn Debug off as it can be a serious performance hit on your router.
There are several commands for turning off Debug.
Router# no debug
If you type debug ?, you will see that there are over 200+ Debug commands, and each of those has many options. Debugging RIP is just a very simple example.
Troubleshoot Cisco routers and switches using the debug commands - Part 1
What makes Cisco IOS Debug commands so useful?
Cisco IOS Show commands can tell you many things about what is going on with your router or switch, but they can’t tell you everything. For example, Show commands cannot tell you when routes drop in or out of the routing table, why an ISDN line failed to connect, whether a packet really went out the router, or what ICMP error code was received. On the other hand, Cisco IOS Debug commands can tell you all these things, and more.
Besides providing more detailed information than what Show commands can provide, Debug commands have the benefit of providing information in “real time” (or dynamically). This is contrary to Show commands that just take a snapshot in time and display the results on your console (somewhat static results). This real-time difference can be very helpful in diagnosing problems.
Tuesday, October 7, 2008
How to learn CCNA efficiently?
1. I bought both Lammle's book, plus the Cisco PressICND1, and ICND2 books by Wendell Odom
I like Odom's books and as there are two (smaller) ones, I can carry one and read on the train/plane. I prefer the style to Lammle's book, but I'm sure mileage varies.
You should also consider doing a CCNA course or bootcamp. I recently attende one. In the interest of fair disclosure, I work for Global Knowledge!
2. I think the best advice I can give you regarding the 640-802 is to subnet, subnet and then subnet some more. Only when you have a true grasp on the complexities of subnetting and general IP addressing schemes can you really begin to appreciate other topics.
The CISCO press books are a little dry but they are packed with the information required. I would probably then plump for a ExamCram volume as a reference point in the last few weeks before the exam. These books will not teach you the topics in any great depth but they can act as good benchmarks.
3. Lammlee's book is a good resource. I also used the Transender practice exams and purchased a couple of routers and switches off ebay to practice on. I was able to pass the ICND1 on the first attempt using only these resources. (I decided to go the two-exam route)
The ICND2 exam is a little tougher IMO. Make sure you understand spanning tree, OSPF, NAT/PAT.
4. Odom's (Cisco Press) ICND1 and ICND2 and both are excellent.
I used Odom's ICND1 to prepare for the 1st exam. I followed his study plan recommendations and did very well on the exam.
I'm using Odom's ICND2 now to prepare for next exam and my studies appear to be going well. Below is a summary of what I'm doing.
- I'm using both the ICND1 and ICND2 texts to prepare as if I'm studying for the composite (640-802) exam. I've found this helps me better understand topics covered in ICND2 text.
- After I read a topic in ICND2, I go back through the material and practice the commands and configurations on my home lab. I go over and over the 'show' commands used.
- I spend 3-4 hours a week getting more hands-on to drill in what I've covered to date.
I tend to recall commands and show output much better from hands-on than from the text. I may be wrong but it seems that way to me.
I purchased Lammle's text for the composite (640-802) exam thinking I would read it in conjunction with the Odom texts. Again, maybe it's just me, but that didn't work well for me. In fact, I pulled Lammle's text off the shelf tonight to read his section trunking, vtp, etc. I had already covered the material in Odom's text and I thought Lammle's would help me catch anything I missed. Didn't work. In fact, I stopped and put it back on the shelf because I didn't want it to confuse me. (It also appears to me that Lammle doesn't devote as much time as I need to some topics.)
5. There are a number of resources, Mirza - to some degree it depends on how you learn best.
I've posted above two sets of books (Lamie and Odom) that for me are very good. I guess these are a great starting point.
In addition to this, you might consider taking a training course. I'm biased because I work there, but take a look at Global Knowledge's classes (www.globalknowledge.com, or www.globalknowledge.net). Depending on how much you can do youself, consider the CCNA bootcamp vs the ICND1/ICND2 classes.
Getting some real hardware or a good simulator is also important. Boson's product looks pretty good, and there'a an open souce product (but that needs actual IOS images that may not be readily available to you). But picking up a couple of switches and a router should not be too expensive (ebay to the rescue).









