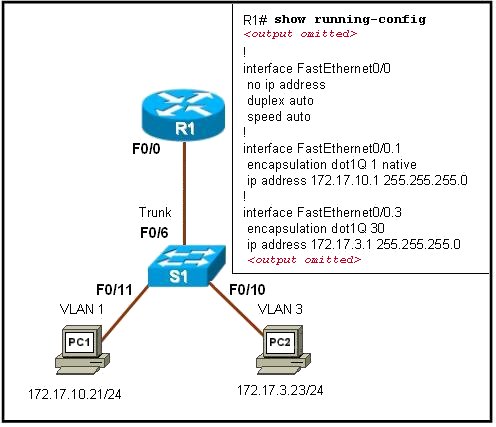
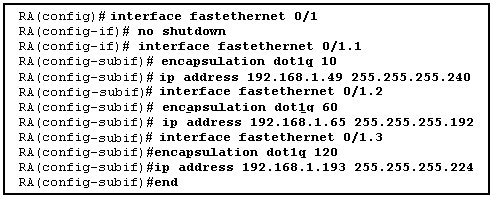
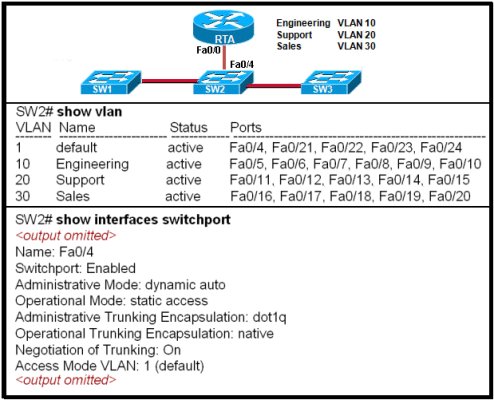
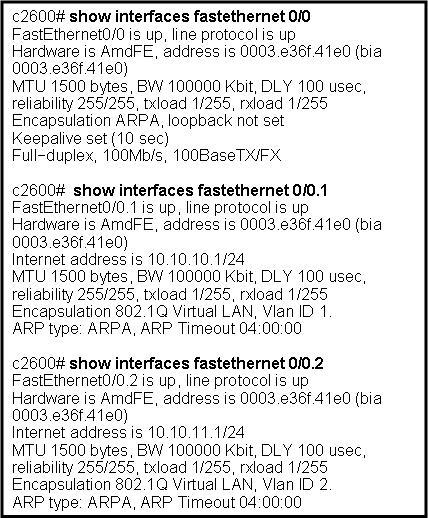
VTP SIM
Question:
This task requires you to use the CLI of Sw-AC3 to answer five multiple-choice questions. This does not require any configuration.
To answer the multiple-choice questions, click on the numbered boxes in the right panel.
There are five multiple-choice questions with this task. Be sure to answer all five questions before leaving this item.

Important: The VTP simlet has a pool of 10 question . Test may have only 5 Questions for VTP SIM
some very usefull commands to answer this simlet:
show cdp neighbor , show cdp neighbor detail , show interface trunk or switchport , show mac-address-table, show spanning-tree, show vlan , show vtp status , show run .
The pool of 10 questions are discussed here starting with the 4 questions in the above picture.
Question 1 :
What interface did Sw-AC3 associate with source MAC address 0010.5a0c.ffba ?
Answer:
Fa 0/8 (As per the picture above)
To find out the associate interface number for a given mac address on the switch use the show mac-address-table command and search for the mac address 0010.5a0c.ffba and its associated interface number.
Question 2 :
what ports on Sw-AC3 are operating has trunks (choose two)?
Answer:
Fa 0/9 and Fa 0/12 (As per the picture above)
To find out the ports operating has trunks on a switch
Use the show interface trunk command this will display all the trunk ports configured on switch.
(or)
Use the show interface switchport command and check the output of the command for operational mode : type trunk for each and every interface.
Question 3:
What kind of router is VLAN-R1 ?
Answer:
2611 ( as per picture above)
To know details of directly connected Neighbor, use the following command on the switch show cdp neighbors command, this output gives the following details about its neighbors
Device ID, Local Interface ,Holdtme, Capability, Platform, Port ID
To know what kind of router is VLAN-R1 we need to identify its platform details from above command output.
Question 4:
Which switch is the root bridge for VLAN 1 ?
Answer:
Sw-AC3 (As per the question above in picture)
Step1: Use the Show spanning-tree vlan 1 command this output provide the mac address of the root bridge.
Step2: now use the show mac-address-table command this output associates the mac address to a interface number.
Step3: use the command show cdp neighbors this output will give us the local interface associated with the hostname(Device ID).
Question 5 :
Out of which port on switch Sw-Ac3 would a frame containing an IP packet with destination address that is not on a local LAN be forwarded?
Answer:
To forward any packet with destination address other then the subnet network of the switch, the switch usually forwards this IP packets to the layer 3 device example router connected to it.
Step1: Find the default-gateway(Router or layer 3 device) configured on the switch.
use the Show run command to view the IP address used to configure default-gateway on the switch.
Step2: Look for the router VLAN-R1 after using the show cdp neighbor detail command
Sample output of show cdp neighbor detail command for better understanding the output details
Device ID: C2950-1
Entry address(es):
Platform: Cisco WS-C2950T-24, Capabilities: Switch IGMP
Interface: FastEthernet0/0, Port ID (outgoing port): FastEthernet0/15
Holdtime : 139 sec
Two things to notice from above output
Interface: FastEthernet0/0 this statement provides that the neighbor(c2950-1) is connected to fa 0/0 on the c3660-2 local switch.
Port ID (outgoing port): FastEthernet0/15 this explains that neighbor (c2950-1) uses fa 0/15 port to reach c3660-2 switch.
FOR OUR QUESTION WE SHOULD LOOK FOR THE ROUTER VLAN-R1 corresponding details and to which port it is connected on local switch Sw-Ac3.
Step3: The port number to which the routerVLAN-R1 is connected on switch Sw-Ac3 is used to forward the packets with destination address that is not on a local LAN.
Question 6:
What address should be configured as the default-gateway for the host connected to interface fa 0/4 of SW-Ac3 ?
Answer:
Step1: Find the details of the VLAN assigned to interface fa 0/4 by using the show vlan command on Sw-Ac3.
The above exhibit question has fa 0/4 configured has VLAN1 based on the output from show vlan command.
Step2: From the exhibit question we know that VLAN1 is configured on router using sub-interface fa 0/0.1 with IP address 192.168.1.254 /24.
Step3: 192.168.1.254 should be configure as default-gateway address for the host connected to fa 0/4 on switch.
Because VLAN1 corresponds to fa 0/4 on Sw-Ac3 and host connected to fa 0/4 will be member of vlan1.
Question 7:
Out of which ports will frame with source mac-address 0015.5A0Cc.A086 and destination mac-address 000A.8A47.0612 be forwarded ?
Answer:
Step1: Use Show mac-address-table command on the switch.
The output of a show mac-address-table provides the mapping of mac address with port numbers. Search the output for the two mac-addresses provided in the question and select the destination mac address corresponding port number for correct answers.
Step2: If you do not find the above destination mac-address in SHOW MAC-ADDRESS-TABLE output , then the frame will be broadcast or flooded to all ports ( all ports may be ports of particular vlan on switch ,Selection of VLAN will be depending on the source mac-address port vlan membership) except the port it recieved from.
Question 8:
From which switch did Sw-Ac3 receive VLAN information ?
Answer:
Step1: Use Sw-Ac3#show vtp status command .
Sample output of show vtp status command
switch# show vtp status
VTP Version : 2
Configuration Revision : 255
Maximum VLANs supported locally : 1005
Number of existing VLANs : 35
VTP Operating Mode : Server
VTP Domain Name : Lab_Network
VTP Pruning Mode : Enabled
VTP V2 Mode : Enabled
VTP Traps Generation : Disabled
MD5 digest : 0x08 0x7E 0x54 0xE2 0x5A 0x79 0xA9 0x2D
Configuration last modified by 127.0.0.12 at 8-7-02 11:21:43
Local updater ID is 127.0.0.12 on interface EO0/0 (first interface found)
The local updater ID in the above output identifies the ip address of the device which is providing the VLAN information. The address could also be of the switch itself.
Step 2: Show cdp neighbor detail provides the hostname for corresponding to that IP address.
Question 9:
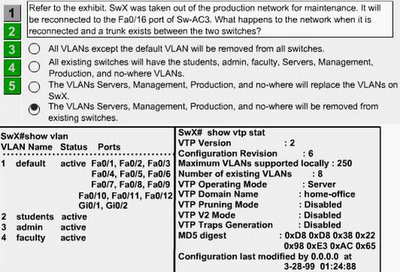
Refer to the exhibit. SwX was taken out of the production network for maintenance. It will be reconnected to the Fa 0/16 port of Sw-Ac3. What happens to the network when it is reconnected and a trunk exists between the two switches?
Answer:
Step1: On switch Sw-Ac3 use show vtp status command. Notice the output for domain name, Both switches must have same domain name configured to exchange vtp messages (exhibit domain name: home-office ).
Step2: If domain name matches, Then note Configuration Revision number of the Sw-Ac3 and compare it with the SwX , Whichever switch has highest configuration revision number will become the vtp updater. The switch which becomes vtp updater will replace other switch vlan information with its own vlan information.
Example if SwX revision number is highest , Then VLAN information that is configured in Sw-Ac3 will be replaced by the VLAN information in the SwX.